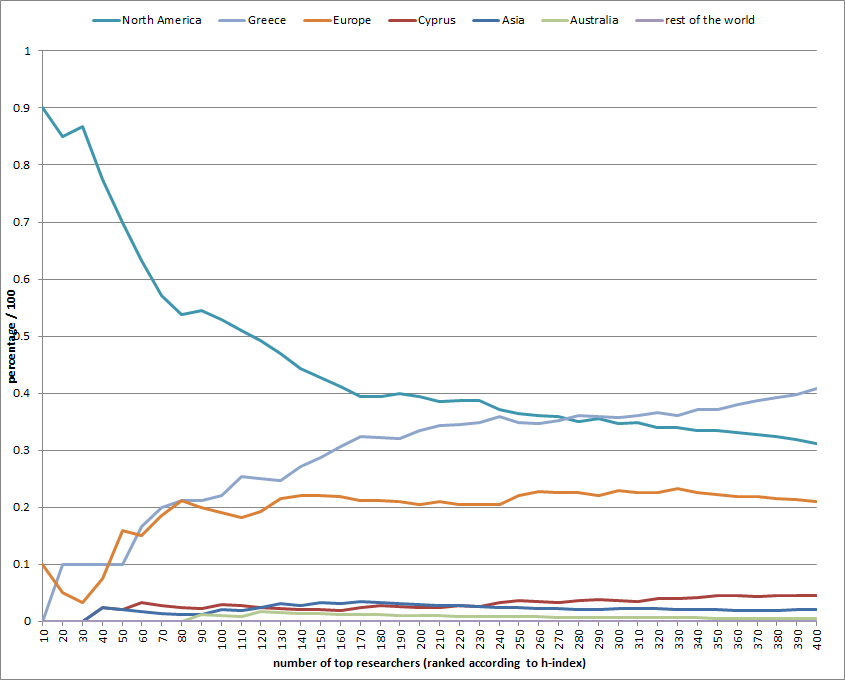
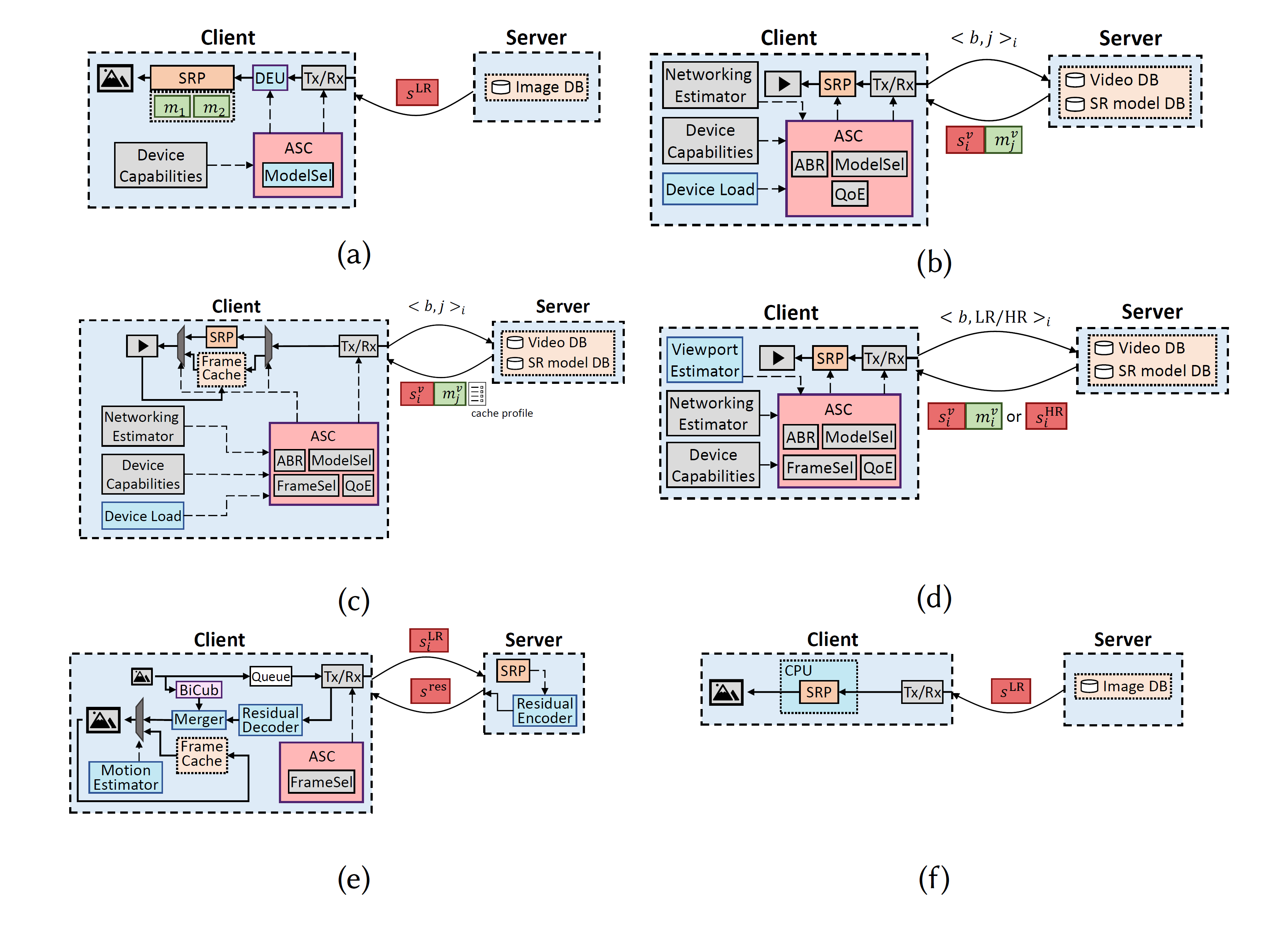
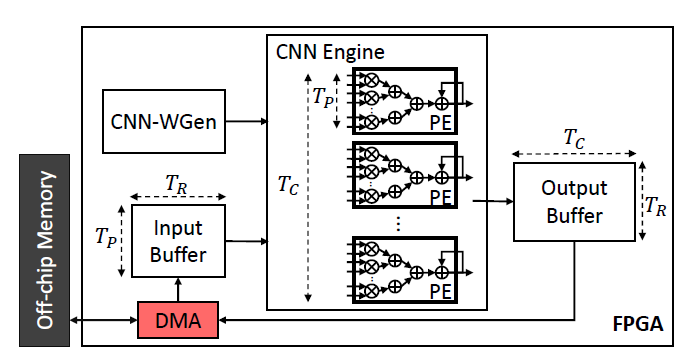
Dynamic interaction in knowledge based systems: An exploratory investigation and empirical evaluation | Request PDF

Ioannis Paparrizos's research works | École Polytechnique Fédérale de Lausanne, Lausanne (EPFL) and other places

Ioannis Paparrizos's research works | École Polytechnique Fédérale de Lausanne, Lausanne (EPFL) and other places
PDF) Adoption of Biometric Authentication Systems: Implications for Research and Practice in the Deployment of End-User Security Systems

PDF) A Critical Approach to Privacy Research in Ubiquitous Environments – Issues and Underlying Assumptions